Zero Trust Architecture: The Future of Cybersecurity
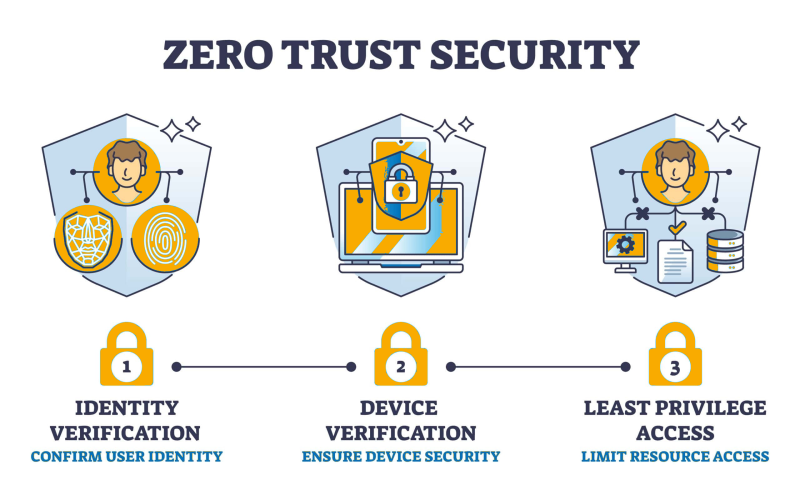
Zero Trust Architecture enhances cybersecurity by eliminating implicit trust, enforcing strict access controls, and securing digital environments.
What is Zero Trust Architecture?
Zero Trust Architecture (ZTA) is a cybersecurity framework that operates on the principle of "Never Trust, Always Verify." Unlike traditional security models that assume internal networks are safe, Zero Trust requires authentication, authorization, and continuous monitoring of all users and devices—whether inside or outside the organization.
ZTA eliminates implicit trust and enforces strict access controls using multi-factor authentication (MFA), least privilege access, micro-segmentation, and real-time monitoring to secure networks, applications, and data.
Why Should Organizations Adopt Zero Trust Architecture?
Zero Trust is becoming the gold standard for cybersecurity due to the increasing risks of cyber threats, ransomware attacks, and insider threats. Here’s why organizations should adopt it:
✔️ Eliminates Implicit Trust – Prevents unauthorized access even within the corporate network.
✔️ Enhances Data Security – Protects sensitive data from cyber threats and insider risks.
✔️ Reduces Attack Surface – Limits access to critical resources, reducing the risk of breaches.
✔️ Improves Compliance – Meets regulatory standards like GDPR, HIPAA, and NIST.
✔️ Enables Secure Remote Work – Ensures secure access to company resources from anywhere.
How to Become a Zero Trust Cybersecurity Specialist?
With organizations prioritizing Zero Trust security, skilled professionals are in high demand. Follow these steps to build a career in this domain:
1. Learn the Fundamentals of Cybersecurity
📌 Gain a strong understanding of network security, authentication, access control, and encryption.
📌 Study cybersecurity frameworks like NIST, CIS Controls, and ISO 27001.
2. Master Zero Trust Principles
📌 Understand least privilege access, micro-segmentation, and identity verification.
📌 Learn how Multi-Factor Authentication (MFA), Single Sign-On (SSO), and identity management solutions work.
3. Get Hands-on Experience with Zero Trust Technologies
📌 Gain practical experience in Zero Trust Network Access (ZTNA), Software-Defined Perimeter (SDP), and cloud security.
📌 Work with identity providers (Okta, Azure AD), SIEM solutions (Splunk, IBM QRadar), and endpoint security tools.
4. Earn Relevant Certifications
Certifications enhance credibility and job prospects:
✔️ Certified Information Systems Security Professional (CISSP)
✔️ Certified Ethical Hacker (CEH)
✔️ Zero Trust Security Certification (offered by vendors like Microsoft, Palo Alto, or Forrester)
✔️ Certified Cloud Security Professional (CCSP)
5. Stay Updated with Cybersecurity Trends
📌 Follow industry leaders, read cybersecurity blogs, and participate in security forums.
📌 Attend conferences like Black Hat, DEF CON, and RSA Conference.
Roles & Responsibilities of a Zero Trust Security Specialist
A Zero Trust specialist is responsible for designing, implementing, and maintaining Zero Trust security frameworks within an organization. Their key responsibilities include:
🔹 Assessing and analyzing cybersecurity risks.
🔹 Implementing Zero Trust Network Access (ZTNA) strategies.
🔹 Managing identity and access controls using MFA, SSO, and Role-Based Access Control (RBAC).
🔹 Designing micro-segmentation to prevent unauthorized lateral movement.
🔹 Monitoring security logs and responding to threats in real-time.
🔹 Ensuring compliance with security regulations.
Zero Trust Security Specialist Salary in India & the US
| Location | Entry-Level (0-2 yrs) | Mid-Level (3-6 yrs) | Senior-Level (7+ yrs) |
|---|---|---|---|
| India | ₹8-15 LPA | ₹18-30 LPA | ₹35+ LPA |
| US | $90K-$120K | $130K-$170K | $180K+ |
Cloud security and Zero Trust experts with advanced skills earn significantly higher salaries, especially in banking, healthcare, and government sectors.
Conclusion & Future of Zero Trust Architecture
Zero Trust is the future of cybersecurity. As cyber threats become more sophisticated, organizations are shifting towards Zero Trust frameworks to enhance security and protect sensitive data.
In the coming years, AI-driven security, real-time threat detection, and advanced identity management solutions will further evolve Zero Trust strategies. Cybersecurity professionals skilled in Zero Trust, cloud security, and AI-powered security analytics will have excellent career opportunities in the rapidly growing cybersecurity industry.
Keywords:
Zero Trust Architecture, cybersecurity, Zero Trust security, Zero Trust model, network security, cloud security, Zero Trust specialist, MFA, ZTNA, cybersecurity jobs, Zero Trust certification, IT security, cybersecurity salary, data protection, micro-segmentation, access control.



Write A Comment
No Comments